Table of contents
sudo apt update && sudo apt install netdiscover nmap arp-scan
#installing the tools
"nmap"
"nmap" is derived from Network Mapper. It is an open-source network discovery and security auditing tool widely used by network administrators for many types of scanning. It can detect open ports, services running on those ports, operating systems of the target machines etc. by sending packets to target hosts and analyzing the responses to determine the characteristics of the network.
There are a variety of scans that can be performed using "nmap"; among which are:
TCP SYN scan: used to perform a stealthy TCP port scan that sends a SYN packet to the target system's ports and analyzes the responses to determine whether the port is open, closed, or filtered(by a firewall). It is also known as half-open scanning as it does not complete the TCP three-way handshake in its scanning process.
nmap -sS -V <remote ip address> #note: command has to be run as root
To demonstrate, I will be using two Ubuntu machines running on Virtualbox.
The result shows how much time the scan took, the MAC address of the destination host, the open ports etc.
By default, nmap scans the most common 1000 ports for each protocol (tcp and udp). We can see that two ports are open (ssh and http) and 998 closed ports.
The "-V" flag displays extra information about the services that are running on the open ports. A non-root user can run the "nmap" TCP Connect scan.
TCP Connect scan: used to perform a less stealthy TCP port scan, but more reliable than a TCP SYN scan, as it completes the TCP three-way handshake in its scanning process. This is the default "nmap" scan for non-root user.
nmap -sT -V <remote ip address>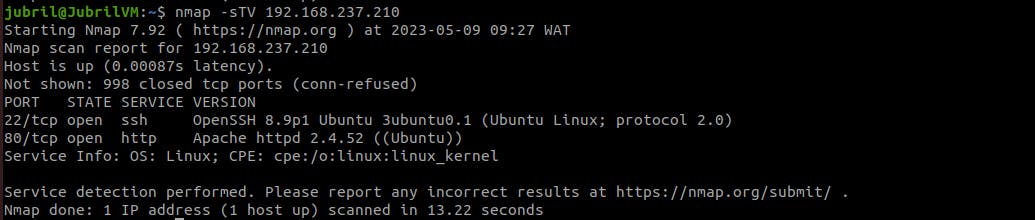
UDP scan: used to perform UDP port scan
nmap -sU <destination host> #must be run as rootICMP scan: used to perform ICMP Ping scan to identify hosts on a network and determine which ones are active and responsive.
nmap -sn <destination host>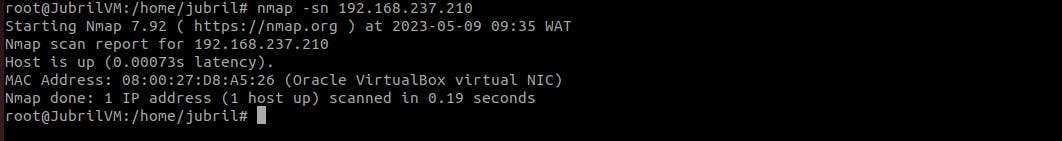
"arp-scan"
Address Resolution Protocol (ARP) is a protocol used to map an IP address to a MAC (Media Access Control) address on a local network.
"arp-scan" is a tool that leverages the ARP protocol to discover devices on a network by sending ARP requests to every IP address on the network and analyzing the responses. It is commonly used by network administrators and security professionals to discover and map the devices on a network.
ARP scanning is useful in discovering hosts on the network that want to remain hidden by not responding to requests like ping, TCP or UDP scans. This is because "arp-scan" operates at the ARP-protocol level which is a lower-level protocol than ICMP(ping) or TCP/UDP.
Since ARP is not routable, this type of scanning works only on a local area network. you can find wired or wireless hosts connected to the same LAN. If a device responds to the ARP request, "arp-scan" can determine its IP address and MAC address.
arp-scan -I <name of interface> -l
#must be run as root
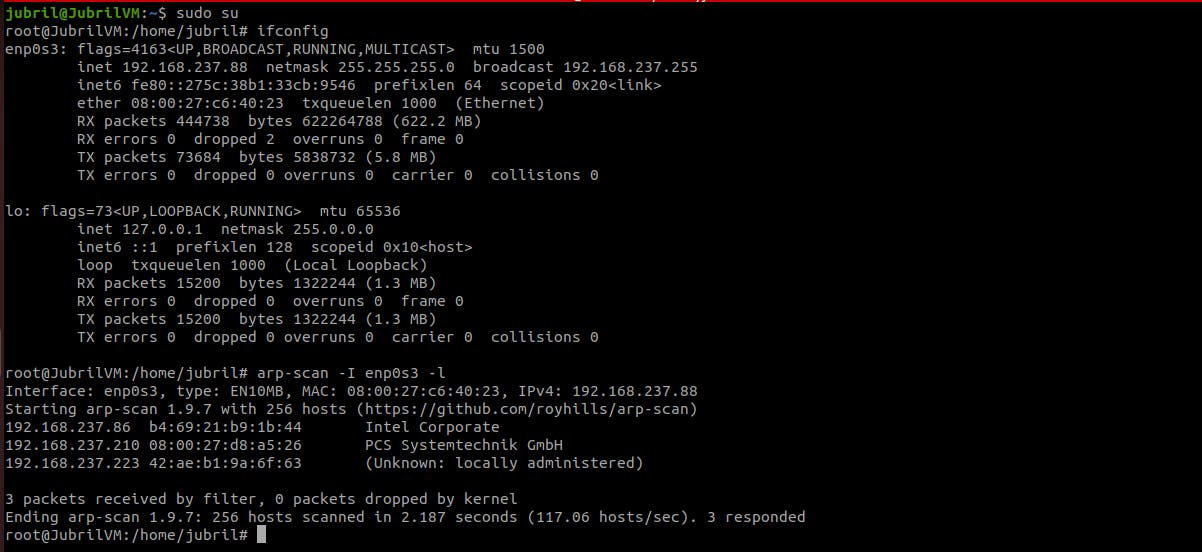
"ifconfig" - to confirm the name of the network interface
The result shows the hosts on the LAN.
"arp-scan" is very noisy. An intrusion detection system could find out that a scan is running. To perform a stealthier arp-scan, you can use another tool called "netdiscover".
"netdiscover"
This is both an active and passive arp reconnaissance tool.
The active mode of "netdiscover" actively sends arp requests packet to discover the other hosts on the network. It runs continously until you stop it.
sudo netdiscover -i <name of the interface>
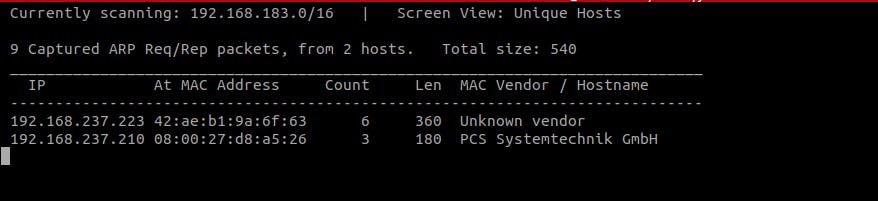
The passive mode of "netdiscover" ensures an "arp-scan" is done in a stealthy mode. In this mode, "netdiscover" does not send arp requests, it only sniffs the traffic and monitors the arp requests sent by other hosts on the local network. ARP request packets are sent to the broadcast address, hence, each host on the LAN receives the packet.
add the "-r" flag to scan passively.
sudo netdiscover -i <name of the interface> -r
Voila! QED!